ETIC Certificate
Working in the ETIC lab provided me with a unique perspective on technology and innovation. Observing senior students engaged in their projects sparked my interest and enhanced my understanding of the practical applications of our coursework. Witnessing their dedication and creativity inspired me to delve deeper into my projects and explore new avenues of research. The collaborative atmosphere of the lab encouraged me to seek mentorship and guidance from experienced peers, fostering my growth as a technologist. Overall, my experience in the ETIC lab has not only broadened my perspective but also fueled my passion for exploring the boundless possibilities of technology. I have demonstrated proficiency in configuring wireless routers, conducting network analysis using tools such as Wireshark and NMAP, and setting up servers, including the installation of Ubuntu on the Class C Windows server. Collaborating with my peer, we efficiently deployed and troubleshooted the network. This certification acknowledges our mastery of essential networking concepts and practical skills gained through hands-on experience and teamwork. We extend our sincere gratitude to our Professor director of the Entrepreneurship and Technology Innovation Center for his unwavering support and guidance throughout this certification journey. His knowledge and guidance have been essential in shaping the achievements of New York Tech and its peers.
Saneen Pervez
spervez@nyit.edu
May 14, 2024
CSCI 362/662 Information
Security Engineering &
Administration Spring 2024
Professor Nizich
College of Engineering & Computing Science

S and P Tech
Company Description:
By offering cutting edge solutions in cloud computing, digital transformation, software
development, and cybersecurity, S and P Tech positions itself as a forward-thinking IT firm. S
and P Tech was accepted since it integrates superior expertise and advances intelligently,
assisting businesses in thriving in the digital sphere. S & P Tech has assembled a group of
individuals who collaborate well and consistently generate fresh concepts. They are committed
to going above and above for their clients and delivering real results.
Network Design:
1. Devices:
S and P Tech keeps up with an experienced networking architecture to facilitate its activities. Our
network architecture is set up of:
- 16 PCs
- 7 Laptops
- 4 Servers
- 4 Routers
- 4 Firewalls
Our five controlling servers are highly skilled due to their superior graphic cards because they
are specifically designed for advanced AI and machine learning tasks in our tech network
architecture. Our next-generation firewalls secure our digital borders, and these multifunctional
routers make sure we’re always connected to keep everything operating efficiently and safely.
Additionally, we’ve installed a complex network behind the scenes that links all of our devices
together smoothly. Special VLANs provide an additional degree of protection by isolating and
safeguarding our network.
• Sector: A technology firm offering innovative solutions.
• Base: Main office situated in New York, alongside branch offices in key global cities.
• Scale: Small-scale operation, boasting a workforce of around 30 professionals.
• Niche: Focused on crafting and executing cutting-edge media and entertainment platforms.
• Clientele: Tailors solutions for a diverse array of customers, including media conglomerates,
live event venues, sports arenas, luxury resorts, and multinational corporations.
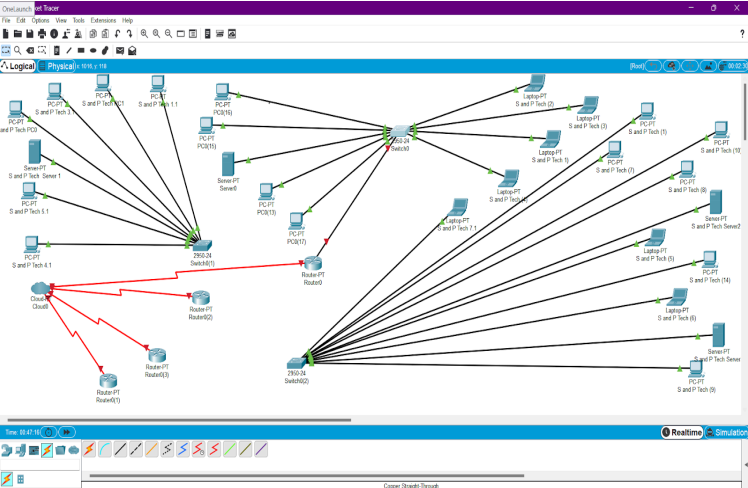
Here’s a visual representation using Packet Tracer of the network setup for our fictional
organization:
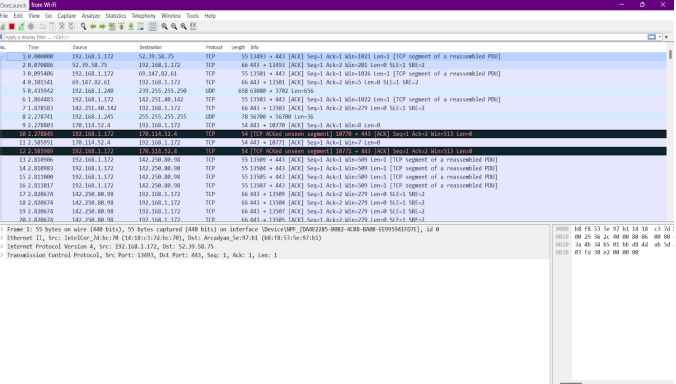
Here’s a practical example of how you can utilize Wireshark to analyze your network for Telnet packet transmissions.

Here’s a practical demonstration of using NMAP to determine which ports are accessible on a server within your network:

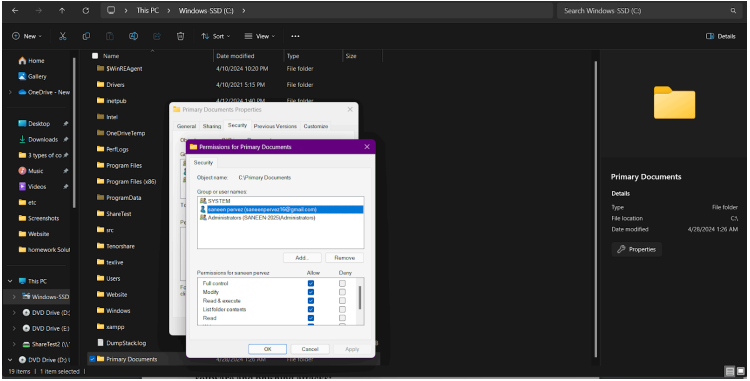
A functional example of how you would “Create,” “Share,” and “Secure” a server file folder called Primary Documents on your network:

A simple policy to direct users on how to identify and avoid malicious software and phishing attacks:
- Watch Your Emails: Be careful with emails from people you don’t know or with strange links or files attached.
- Strong Passwords: Make sure your passwords are strong and unique. Don’t share them with anyone, and turn on that extra security thing if you can.
- Keep Things Updated: Make sure your computer and programs are always up to date. It helps keep the bad stuff out.
- Stay Safe Online: Be careful with websites that don’t look right or ask for personal info. And watch out for those pesky pop-up ads.
- Stay in the Know: Join in on those security training sessions and follow all the rules of our company’s policy. None of our info should be shared to outsiders.
- Speak Up: If something seems fishy, let the IT sector know right away. They’re here to help keep us safe.
An example of one of your company’s documents both in its unencrypted and encrypted versions, created with the RSA
algorithm and a public key:

Conclusion:
I now have a better understanding of security analysis, network design, and best practices for protecting organizational assets. My grasp of cybersecurity fundamentals has improved as a result of my practical experience with tools like Wireshark, NMAP, and encryption methods. I’m also better equipped to handle difficulties related to network and data security in the real world. After doing this project, I feel like I have more practical experience—almost like a cybersecurity analyst. I’m gaining experience with cybersecurity technologies like WireShark, NMAP, and Cisco Packet Tracer by enrolling in a summer internship program. These tools will help me in my future job. I’ve learned useful skills from this assignment, including how to create a fictional corporation from the ground up, build its network infrastructure, and become proficient with tools like Wireshark and NMAP for investigation of networks. In addition, I’ve gained knowledge on how to create user-friendly regulations and secure server file folders so that colleagues can be taught how to identify and steer clear of online dangers like malware and phishing scams. Exploring encryption algorithms was one of the most fascinating parts of this endeavor. I had a great experience that increased my understanding of data security when I learned how to protect important corporate papers using public key encryption and the RSA algorithm. In summary, this project has broadened my understanding of network architecture and security protocols while also offering me useful perspectives that I can utilize in actual information technology situations.
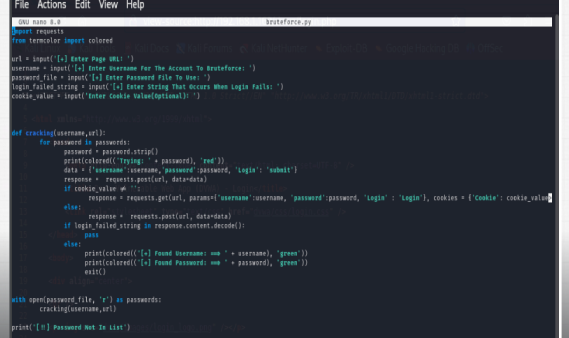
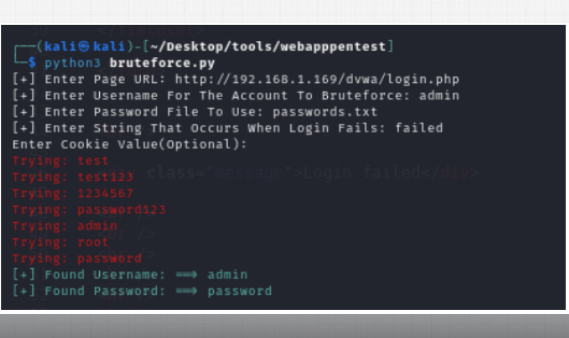
Login Bruteforce, Directory Discovery
In the first part of the project we tried to break a login password by only knowing the username and in the second program we will see if we can find some hidden directories on a webpage and maybe those directories could be useful for us. Nonetheless both of these programs are going to work similarly. Our login bruteforcer is going to open a txt file with a bunch of passwords and we are going to send each one of those passwords from the file and hope that one of them is the correct one which will grant us access to that account. The second program is going to work by opening a txt file and reading common directory names that we will then request to visit and if we manage to visit them and get the status code 200 that means that that page exists. If we get a connection error, then that means that it doesn’t exist