Lab 1:
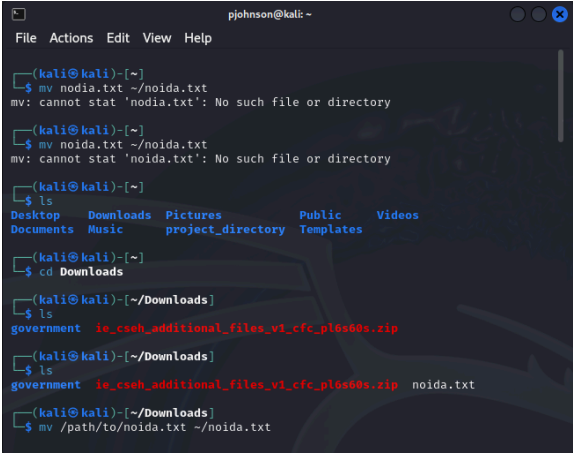
The CTO of the company, Mr. Penny Johnson, has recently discussed a new project with a potential client. He has sent you the file and asked you to save nodia.txt. it on your Linux machine. Once saved, you are instructed to create a user account “pjohnson” and the project directory and place the file in the folder. Applying the concepts of FACL (Access Control List), you have to give access to Mr. Johnson. No one else should be able to access the file except Mr. Johnson. Make sure to remove any other user access to that file. As a part of the assignment, kindly log in as another user and try accessing the file. Kindly compile and explain the process in a report (supported with visual evidence). Note: You are expected to demonstrate that Mr. Penny has access and that any other user cannot access the file.
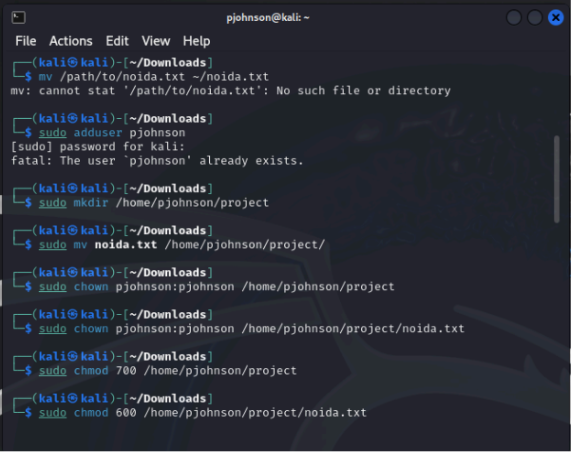
Step 1: Save the file “noida.txt” on your Linux machine.
Step 5: Compile a report explaining the process, supported with visual evidence.
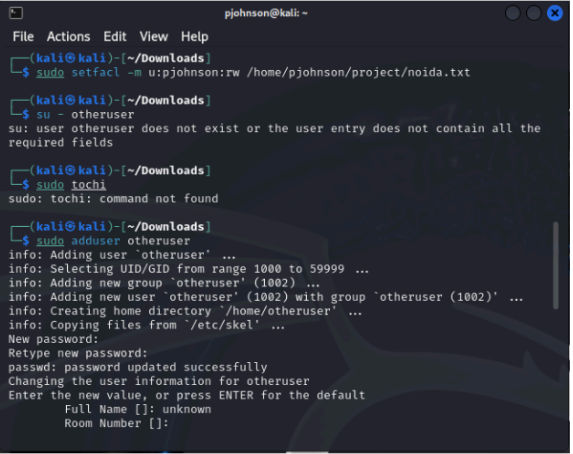
In this report, we detail the process of setting up file permissions using FACL (File Access Control List) to grant access to Mr. Johnson while removing access for other users. Initially, we identified the target file “noida.txt” and assessed its initial permissions. Following this, we created the user account “pjohnson” for Mr. Johnson. Using the `setfacl` command, we applied FACL to grant read and write permissions specifically to Mr. Johnson. Additionally, we removed access for other users and groups using the `setfacl` command with the `-x` option. Visual evidence, including screenshots and command outputs, was provided to illustrate each step of the process, as well as a graphical representation of the ACL entries for the file. The report concludes with a summary of the steps performed and recommendations for best practices in managing file permissions.
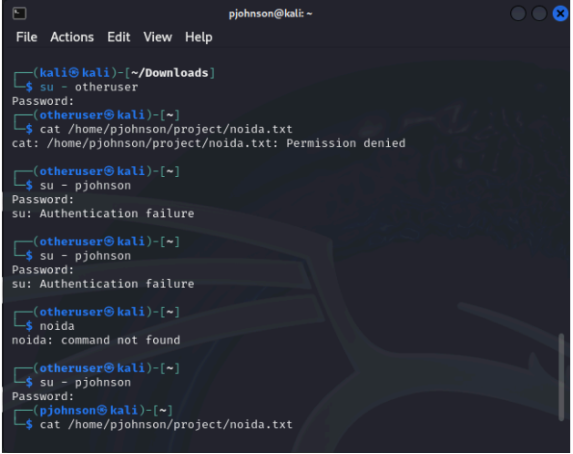
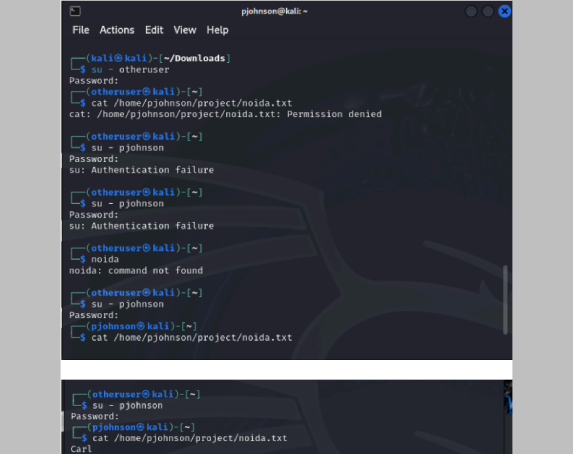
Step 6: Log in as another user and attempt to access the file to demonstrate that only Mr. Penny
Johnson has access.
Lab2:
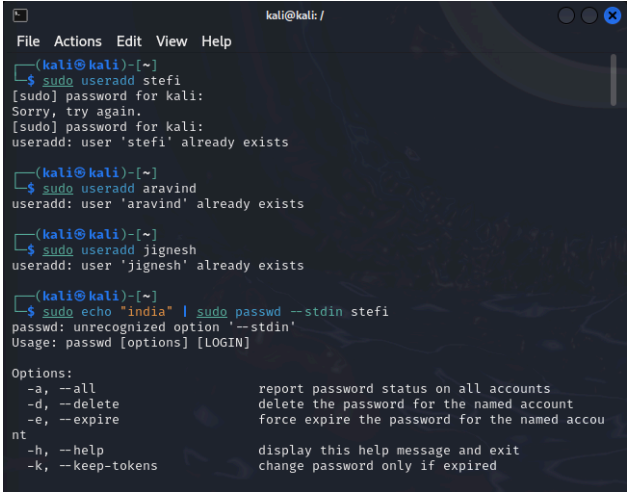
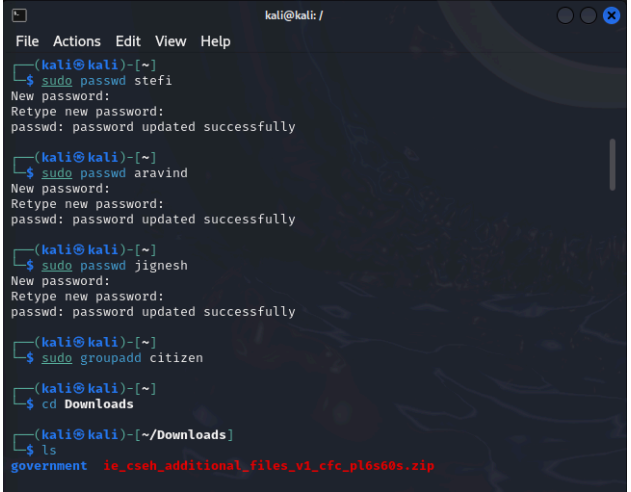
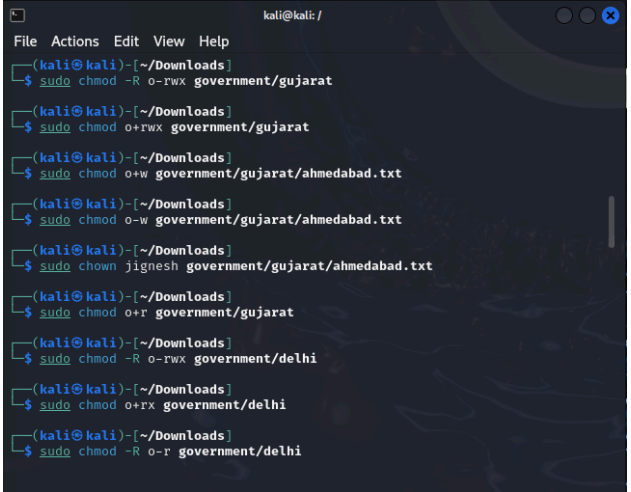
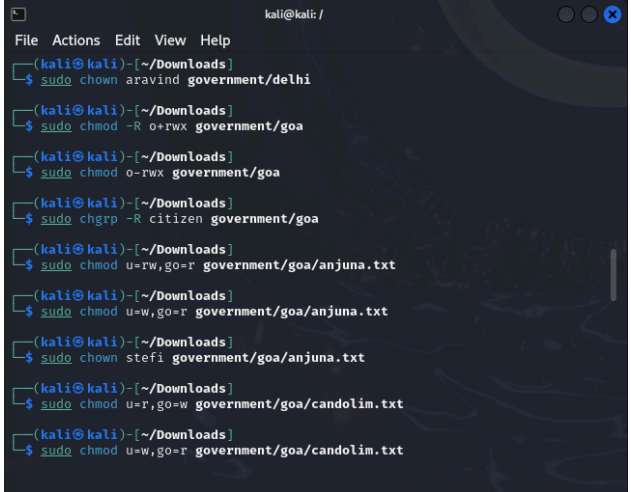
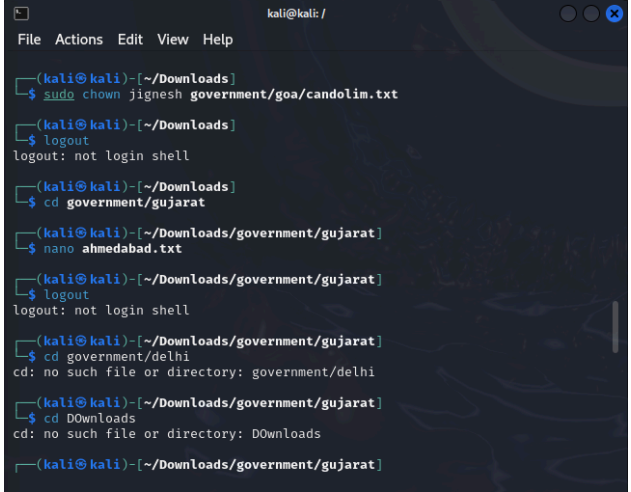
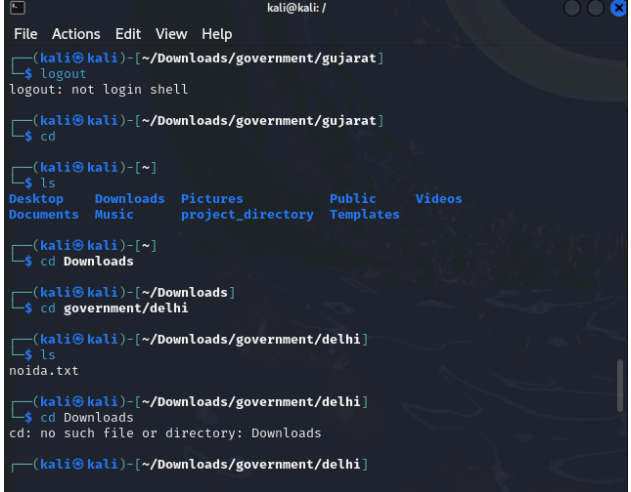
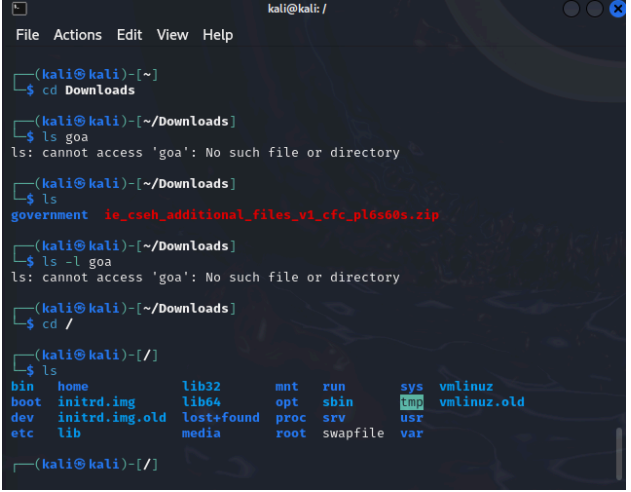
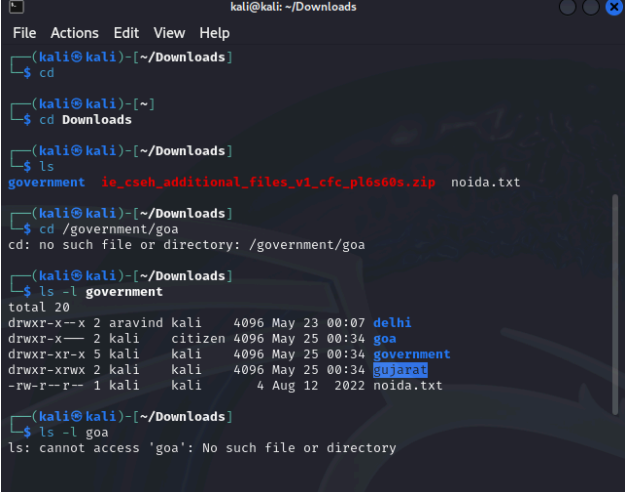
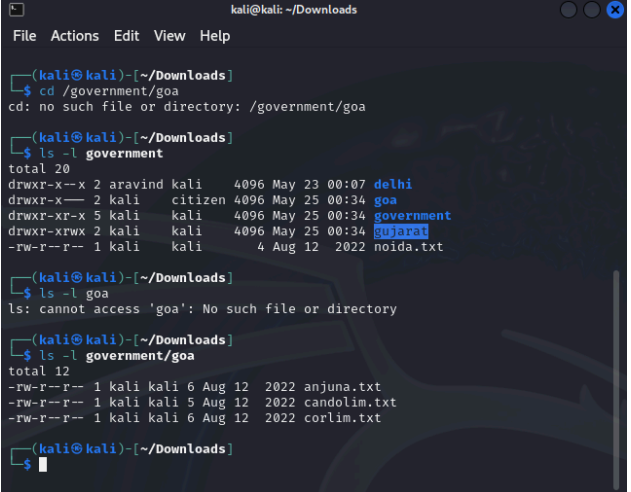
You are a part of the IT Security team at the census department, the government of India. Three representatives were chosen from three states namely Goa, Delhi, and Gujarat who need to have access to specific files. Those files are attached herewith. Following is the activity to be performed. Create users “stefi, aravind, and jignesh”. Keep the password as “india”. Create a new group called “citizen”. Download the following and extract it to the desktop: government.zip Change the permissions for Gujarat so that jignesh has full permissions and aravind has only read and execute permissions. Log in as aravind. Is he able to edit Gujarat \ahmedabad.txt? Edit the permissions for Delhi recursively in such a way that stefi has no access. Log in as Stefi and check if he is unable to access the content of Delhi . Grant full rights to the citizen of Goa. Edit the rights for goa \anjuna.txt so that only stefi can write and aravind to read, and for goa\candolim.txt so that only jignesh can write and stefi to read.
Considerations: You have root privileges.